World Password Day: Will we soon see the death of the password?
The death of the password has been a long-awaited event in the world of cybersecurity. Recent years have seen the development of a number of technologies, such as 2FA – also known as two-factor authentication – and passkeys that could replace it. In this article, we explore these new technologies for you…
Now in its 10th year, World Password Day celebrates every first Thursday in May. The annual event was designed to reflect on password usage and develop better password practices in order to keep us safer.
What’s wrong with password identification?
Passwords have long been considered by cybersecurity experts as a weak link in the security chain, as they are often easy to guess or crack. This because they are designed to be remembered. For the same reason, users often reuse the same password across multiple accounts. So this form of identification is, arguably, as fallible as we are.
According to the 2022 Verizon Data Breach Investigations report, “the human element continues to drive breaches. Whether it is the use of stolen credentials, phishing or simply an error, people continue to play a large part in incidents and breaches alike.”
The research found that 73% of security breaches came from those above-mentioned methods, and others in the top ten. Carelessness was listed as another big factor, associated with errors such as mis-delivery and misconfiguration.
So what’s the answer?
2FA, or two-factor authentication, also known as multi-factor authentication, is a security measure that requires users to provide two or more pieces of evidence to access their accounts or complete a transaction. It adds an extra layer of protection to online accounts, making it more difficult for cybercriminals to steal information.
2FA can come in different forms, including biometric factors like fingerprints or facial recognition, physical factors like a smart card or key fob, or knowledge-based factors like a password or pin. The most common form of 2FA is a combination of a password and a one-time code that is sent to the user’s phone or email.
The rise of password-free authentication has been fueled by the adoption of standards such as FIDO2, which is an open authentication standard that enables password-free authentication using biometrics, hardware tokens, or other means. FIDO2 is backed by a consortium of companies including Google, Microsoft, and Yubico, and is rapidly gaining adoption across the industry.
Speaking on MIT’s Technology Review in 2022, editor-in-chief Mat Honan notes that the process of replacing the password is already underway.
“Enterprise-oriented companies like Okta and Duo, as well as personal identity providers like Google, offer ways for people to log in to apps and services without having to enter a password. Apple’s facial recognition system has taken biometric login mainstream.
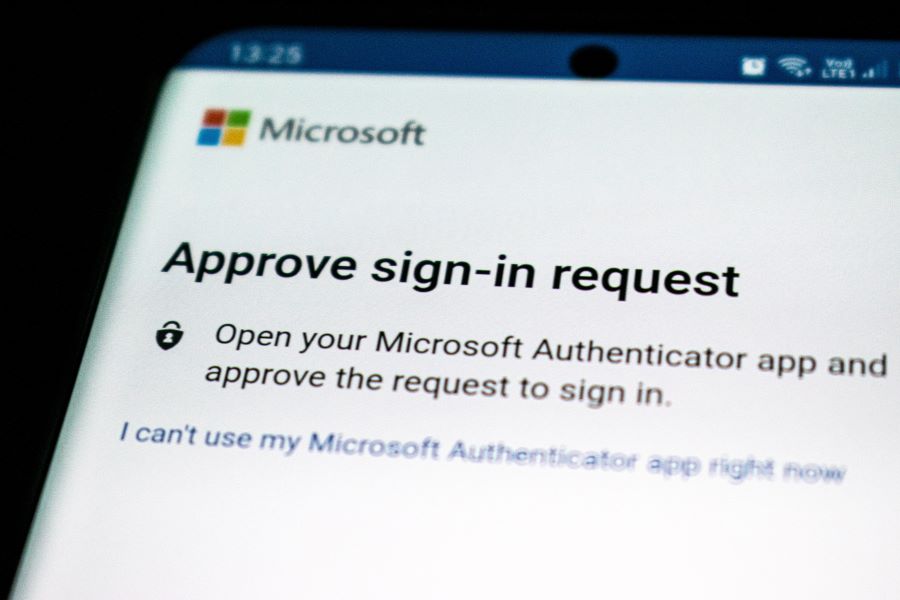
“Most notably, Microsoft announced in March 2021 that some of its customers could go completely passwordless, and it followed up in September by telling people to delete their passwords altogether. Those other methods of authentication? They’re finally winning.”
Speaking via its website, Microsoft commented: “One simple step we can all take to protect our accounts today is adding multifactor authentication, which blocks 99.9% account compromise attacks. The Microsoft Authenticator app is free and provides multiple options for authentication, including time-based one-time passcodes (TOTP), push notifications, and passwordless sign-in—all of which work for any site that supports multifactor authentication. Authenticator is available for Android and iOS and gives you the option to turn two-step verification on or off. For your Microsoft Account, multifactor authentication is usually only needed the first time you sign in or after changing your password. Once your device is recognised, you’ll just need your primary sign-in.”
As well as 2FA, blockchain identity management is a way of securely managing and verifying the identity of individuals or entities using blockchain technology.
It relies on a decentralised network of computers, where each participant maintains a copy of a virtual ledger. Identity information is stored in the form of digital certificates, which are cryptographically signed and stored on the blockchain.
This decentralised approach is said to make it more difficult for hackers to compromise the system, as they would need to attack every node in the network simultaneously. Additionally, users have more control over their own data, and can choose which parties can access their information.
Rohan Pinto, CTO and Founder of 1Kosmos BlockID and member of the Forbes Technology Council, added: “Blockchain identity management is the bane of password-based verification, all the more so because of the development of decentralised identifiers (DIDs). Over time, digital identities will evolve into self-sovereign identities, allowing users to own and independently manage their personal data.
“Passwords were meant to evolve into death. It’s only a matter of time before they actually do.”
For more computing news, click here.

